Resilient Smart Built Environments: Research Directions
Smart Infrastructure is composed of physical and digital Infrastructure. It aims to improve data-driven decision-making and enable the faster and cheaper operation and maintenance (e.g., better whole-life value). As a society, we increasingly depend on 'smart' Infrastructure that is internet-connected and deployed across many sectors around us, such as transportation, energy, water, and, more importantly, buildings.
The concept of 'smart' means we get to enjoy improved services (e.g., efficiency, effectiveness, convenience). Smart infrastructures comprise thousands of connected devices and systems (i.e., IoT systems). Such dependencies also create significant risks as connected systems increase the cyber-physical attack surfaces. A cyber-Physical attack can be defined as a security breach in cyberspace that impacts the physical environment. Cyber-attacks on smart city infrastructures are not only disruptive and costly but could also be fatal. For example, a computer hacker gained access to a city's water system in Florida and tried to pump in a dangerous amount of a chemical [1]. Cyber-attacks are costing UK firms £34 billion annually [2]. Cyber-physical attacks targeting IoT systems cost the UK's economy £1 billion annually and increasing due to the increasing adoption of smart Infrastructure [3]. IoT attacks cost UK businesses £ 244,000 annually, with malware attacks the most common form of breach [3]. Malicious actors constantly try to find sophisticated ways to carry out cyber-physical attacks which aim to evade traditional attack detection techniques. Let us now introduce some of the critical challenges and potential research directions.
Cyber-attacks on smart Infrastructure are monitored through traditional techniques such as Network Traffic Analysis (NTA) [4]. NTA is the process of intercepting, recording, and analyzing network traffic communication patterns to detect and respond to security threats. While acknowledging the merit of NTA, more sophisticated and coordinated cyber-physical attacks may require novel solutions to detect them in real-time. Moreover, malicious actors constantly try to find sophisticated ways to carry out attacks (e.g., Stuxnet, Ukraine, power-grid cyberattack, Florida water poisoning). Therefore, to prevent attacks that evade NTA, we need secondary layers of protection based on cyber-physical behavior to mitigate the weaknesses of NTA.
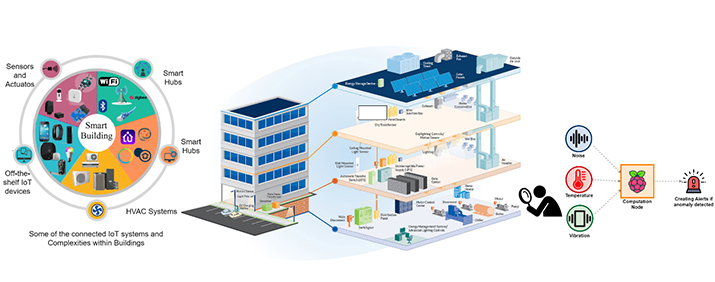
Figure 1: Problem Scenario: if an attacker intends to overheat a system, he could alter the fan behavior (e.g., speed). At the same time, the attacker may also maliciously control the relevant temperature sensors to prevent the reporting of increased temperature.
Buildings are composed of heterogeneous systems. Figure 1 highlights a few different sensing systems that can commonly be seen in modern buildings. First, heating, ventilation, and air conditioning (HVAC) systems perform sensing and actuation. Typically, they are developed by a Building Management Systems (BMS) provider and deployed by a third-party service provider. Secondly, buildings might have sensors built-in (e.g., light, motion) to the Infrastructure of the building or augmented afterward by smart sensing solution providers. Thirdly, off-the-shelf IoT devices and solutions are deployed within the building. These solutions may connect to their service provider over the internet or (fourthly) connected and managed via a local smart hub. Finally, each IoT system mentioned above may use a range of proprietary and open communication protocols at both the application (e.g., MQTT) and physical levels (WiFi, Bluetooth, ZigBee). The takeaway message is that modern smart buildings are a highly complex system that breaks most of the assumptions data science researchers typically have. However, they also create significant opportunities for us to exploit in order t better detect anomaly behaviors within built environments. Each of these sensing systems collects data about different aspects of the building in which we can utilize to detect complex anomalies and malicious activities.
This newsletter highlights three key areas we should focus on as a community of IoT researchers. (1) Multi-Layer Framework, (2) On-the-Edge, and (3) Swarm Intelligence. The objective is to develop techniques to detect anomalies within smart buildings while embracing these principles and better understand their trade-offs.
Multi-Layer Framework
As depicted in Figure 1, each sensing system captures data independently and processes them for their own needs (e.g., HVAC may use sensor reading for automation). As shown in Figure 2, these systems of systems can be conceptualized as series of layers. However, the data captured by these layers could be used (as a secondary use) to generate additional knowledge (e.g., identify anomaly patterns). It is important to note that these systems are configured to operate in their ways, meaning that, at times, we will be able to read what the command would be (if the messages get decrypted within the smart hub). Other times we will only see encrypted packets going back and forth. Suppose the commands are visible (e.g., getting decrypted within the smart hub). In that case, it is easier for the anomaly detection technique to identify anomaly behaviors as it knows the semantic meaning (e.g., kettle switched 'ON').
In contrast, the smart hub can only see packets sent to an external service if the commands are directly forwarded to the cloud in an encrypted format. Though the metadata, such as the size of the packet and destination, could be used to train anomaly detection techniques to infer the command and the originated device (system), it is much more challenging. Therefore, a different set of anomaly detection techniques are required to handle this layer. A potential approach would be to develop multiple anomaly detection techniques organized into a layered framework where each technique would focus on a specific type of anomaly. A key characteristic is to adapt to different systems configurations (i.e., different buildings with varying sensing systems that may be configured to operate in different ways in terms of data types, frequencies, etc.). We have identified four different layers (see Figure 2).
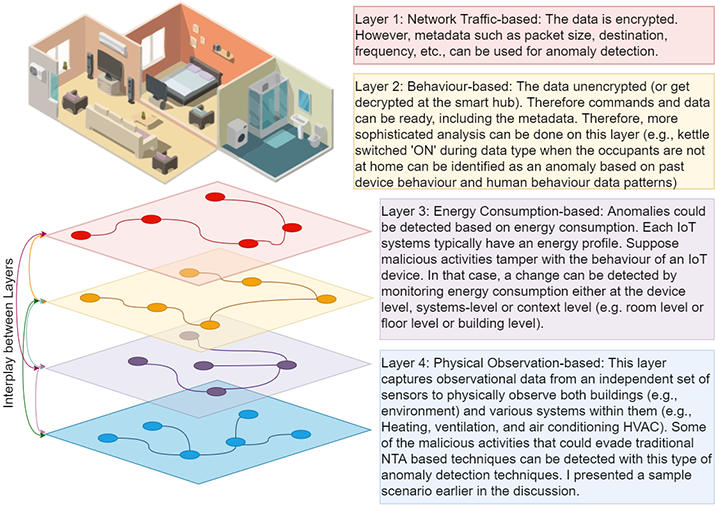
Figure 2: Multi-Layer framework. Each building layout is different. In addition, each IoT system is different in terms of the data types they capture, how often they capture data, whether it is a push-based or a pull-based communication scheme, etc.
On-the-Edge
Most of the current anomaly detection approaches are heavily dependent on cloud resources. For example, a cyber-attack detection system may collect different data types (e.g., network data, metadata, application data) and send them to the cloud. Algorithms run on the cloud could determine whether they are malicious or not activities. However, the downside is that if the network connection is compromised, the attack detection system could also fail to operate. More work has been done on fog systems where fog devices are being deployed to detect malicious activities. Most of the work has been on Raspberry Pi type of devices (single board computers), and model training is mainly done on the cloud, where the detection phase is transferred to the fog layer. While we acknowledge the merit of using fog devices, we propose using edge devices (microcontrollers) to detect anomalies collaboratively. The key advantages of using edge are that they are faster, single-purpose, cheaper, and smaller. Therefore, this approach will utilize edge, fog, and cloud and self-organize to support a given built environment. Further, both fog and edge approaches reduce the dependency on the cloud, increasing resilience.
Swarm intelligence
We consider buildings as living things that could mimic the properties of living things such as self-organization and self-configurations. We expect to sense the environment through many heterogeneous sensors (organized as different sensing systems and layers). There are two types of configurations that need to happen when deploying an anomaly detection system to achieve the best results. First, given the real-world limitations, we need to configure how sensing systems operate to match the anomaly detection techniques requirements. If that is not feasible, anomaly detection techniques must be altered and configured to facilitate the sensing systems' constraints. We call this process self-organization and self-configurations. Typical configuration parameters are (i) what kind of sensors/data types to be used, (ii) what kind of sampling frequency to be used (which could also have a direct impact on the energy consumption of each sensor node), (iii) what kind of anomaly detection technique should be employed, (iv) where the data should be processed (e.g., edge, fog, cloud) and why, etc. We could use swarm intelligence techniques to determine how to configure these parameters optimally to achieve the best outcome in a given context. For example, sensors deployed in a particular room may increase their sampling rate and reconfigure its sensitivity if it detects anomaly heat sources during out of hours. Such an approach could lead to better fire detection compared to current smoke detectors. Similarly, it would also detect whether an occupant forgot to shut the window by opportunistically reconfiguring sensors to detect contextual temperature variations within the room.
The three critical areas introduced in this newsletter can significantly improve the anomaly detection capability within modern built environments.
References
- https://www.bbc.co.uk/news/world-us-canada-55989843
- https://www.telegraph.co.uk/finance/newsbysector/industry/defence/11663761/Cyber-attacks-cost-British-industry-34bn-a-year.html
- https://www.itpro.co.uk/internet-of-things-iot/33702/iot-cyber-attacks-cost-uk-economy-1bn-each-year
- R. Coulter, Q. L. Han, L. Pan, J. Zhang, and Y. Xiang, "Data-Driven Cyber Security in Perspective - Intelligent Traffic Analysis," IEEE Trans. Cybern., 2020.
 Charith Perera is a Senior Lecturer at Cardiff University, UK. He received his BSc (Hons) in Computer Science from Staffordshire University, UK, and MBA in Business Administration from the University of Wales, Cardiff, UK, and Ph.D. in Computer Science at The Australian National University, Canberra, Australia. Previously, he worked at the Information Engineering Laboratory, ICT Centre, CSIRO. His research interests are the Internet of ThingsSensing as a Service, Infrastructure and Architectures, Privacy and Security. He is a member of ACM. Contact him at www.charithperera.net
Charith Perera is a Senior Lecturer at Cardiff University, UK. He received his BSc (Hons) in Computer Science from Staffordshire University, UK, and MBA in Business Administration from the University of Wales, Cardiff, UK, and Ph.D. in Computer Science at The Australian National University, Canberra, Australia. Previously, he worked at the Information Engineering Laboratory, ICT Centre, CSIRO. His research interests are the Internet of ThingsSensing as a Service, Infrastructure and Architectures, Privacy and Security. He is a member of ACM. Contact him at www.charithperera.net
 Yasar Majib is a Computer Science graduate from Newport Institute of Communication and Economics, Pakistan, in 2007. He worked in the industry for 11 years before moving back to academics in 2018. He completed a post-graduate degree in Information Security and Privacy from Cardiff University, UK, in 2019. He is currently pursuing a Ph.D. in Computer Science from Cardiff University, UK.
Yasar Majib is a Computer Science graduate from Newport Institute of Communication and Economics, Pakistan, in 2007. He worked in the industry for 11 years before moving back to academics in 2018. He completed a post-graduate degree in Information Security and Privacy from Cardiff University, UK, in 2019. He is currently pursuing a Ph.D. in Computer Science from Cardiff University, UK.
Sign Up for IoT Technical Community Updates
Calendar of Events
IEEE 8th World Forum on Internet of Things (WF-IoT) 2022
26 October-11 November 2022
Call for Papers
IEEE Internet of Things Journal
Special issue on Towards Intelligence for Space-Air-Ground Integrated Internet of Things
Submission Deadline: 1 November 2022
Special issue on Smart Blockchain for IoT Trust, Security and Privacy
Submission Deadline: 15 November 2022
Past Issues
September 2022
July 2022
March 2022
January 2022
November 2021
September 2021
July 2021
May 2021
March 2021
January 2021
November 2020
July 2020
May 2020
March 2020
January 2020
November 2019
September 2019
July 2019
May 2019
March 2019
January 2019
November 2018
September 2018
July 2018
May 2018
March 2018
January 2018
November 2017
September 2017
July 2017
May 2017
March 2017
January 2017
November 2016
September 2016
July 2016
May 2016
March 2016
January 2016
November 2015
September 2015
July 2015
May 2015
March 2015
January 2015
November 2014
September 2014


