My Kettle Hacked What?!
The Internet of Things (IoT) is growing rapidly, and the number of security incidents involving IoT products even more so [1]. The resulting distrust of IoT products is a major inhibiting factor in the development of the IoT’s social and business objectives of reaching billions of products in the coming years [2].
Industry and regulators worldwide are looking at security testing/evaluation as a possible solution to the security problems introduced by IoT [3], as even the simplest measures addressing security concerns facilitate and accelerate the adoption rate of IoT solutions [4]. Most of these initiatives take a silo approach and look at each and every type of product separately [5] with seemingly different requirements, resulting in the re-evaluation of underlying platforms over and over. Not only is this wasteful, but it will also never scale large enough: there are millions of IoT products [6].
The Risk of IoT Products
IoT products need to protect the important assets they handle [7], such as:
- people’s privacy [8] (e.g. IP cameras),
- access to locations (e.g. connected door locks), and even
- life and limb (e.g. connected cars),
not to mention assets such as pay-for-use features, intellectual property and trade secrets.
Even without these assets, due to their connectivity IoT products still have to protect:
- their privileged connection to the network and services they are connected to [9],
- the passwords they hold [10], and
- the impact they may have on the environment [11].
In other words, IoT product security is important. But it is surprisingly difficult to evaluate.
Even “Simple” IoT Products Are Complex
Although a “simple” IoT product such as a connected kettle [12] may not look very complex, it is in fact an arrangement of several individual hardware and software components providing functionalities such as encryption/decryption, memory management, random number generation, (real-time) operating system, and of course the application that performs the actual functions of the product.
Each of these components is complex in and of itself, with many potential entry points for attacks that might result in subversion of the entire product. This has previously happened with at least one vulnerability in one kettle [12].
Security Is Difficult to Achieve for Product Developers
IoT product development is focused on making a product that performs a function well. It is not focused on security. After all, as customers see their kettle boil water, they do not see a TLS 1.3 secure channel with full X.509 certificate chain verification.
Even if product developers expend effort on security, they rely very much on the security of the underlying platform. And these platforms, too, struggle to show that their security features are really secure.
The Real Issue of IoT Product Security
In theory, all these problems could be solved by more evaluations – many more evaluations. In practice, there will simply be too many IoT products for this to be feasible.
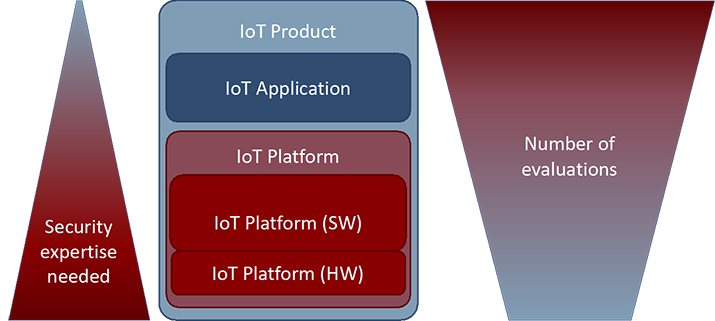
Figure 1: Relation security capability, versus evaluation capacity for IoT Platforms.
Solution to A Big, Difficult Problem: Break It Down into Smaller, Tractable Problems
The sheer volume and diversity of the types of IoT products poses a serious challenge for any approach. The solution is to split IoT products into two layers: a generic platform and a specific application.
The IoT platform and its various components can be thoroughly evaluated by highly skilled evaluation labs with oversight by expert certifiers.
The security of the product can subsequently be built on this solid foundation of the platform and, if necessary, efficiently tested.
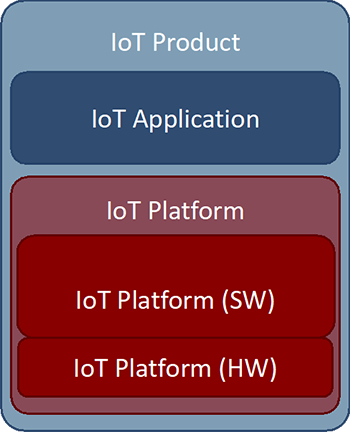
Figure 2: IoT products as the sum of IoT Applications and IoT Platform components.
The application developer can then concentrate their development efforts on the specific functionality to be delivered by the application, rather than on providing security. This way, even IoT product developers with a limited understanding of security would be able to deliver secure solutions.
This approach has the following advantages:
- Reduction of overall development and evaluation effort: A thorough understanding of security will need to be present in a few platform companies, rather than tens of thousands of application developers.
- Reuse of evaluation results: The platforms can be reused by many application developers, which means the costs of a deep security evaluation of a platform can be shared by many application developers rather than be borne by a single one.
- Quick security testing of the application: As the security of a total solution will be provided primarily by the platform, the security evaluation of the total solution can be done cheaply and quickly by checking whether the application uses the platform correctly and a quick test of the application itself.
Conclusion
The security of “simple” IoT products can be assured in an affordable and meaningful way by splitting products into applications and platforms and performing security evaluations on the platforms and security testing on the applications.
Other high-risk applications have adopted similar approaches in the past [13]. It is to be expected that IoT platforms will add much-needed security to IoT products [14].
References
- Alfred NG, “IoT attacks are getting worse -- and no one’s listening”, C|NET, 15 March 2018
- Harald Bauer, Ondrej Burkacky, and Christian Knochenhauer, “Security in the Internet of Things”, McKinsey & Company, May 2017.
- “State of the art syllabus”, ECSO, December 2017 - DCMS, “Mapping Security & Privacy in the Internet of Things”, https://iotsecuritymapping.uk, 2018
- Syed Ali, Ann Bosche and Frank Ford, “Cybersecurity Is the Key to Unlocking Demand in the Internet of Things”, BAIN & Company, June 2018
- Mike Hogan, Ben Piccarreta, “Draft NISTIR 8200: Interagency Report on Status of International Cybersecurity Standardization for the Internet of Things (IoT)”, NIST, February 2018.
Sanjit Ganguli, Ted Friedman, “IoT Technology Disruptions: A Gartner Trend Insight Report”, Gartner, 15 June 2017 - Total Installed Base of 25 Billion Endpoint Units in 2021, “Forecast Analysis: Internet of Things — Endpoints, Worldwide, 2017 Update”, Gartner, 27 December 2017, https://www.gartner.com/doc/3841268/forecast-analysis-internet-things-
- “Looking into the crystal ball: A report on emerging technologies and security challenges”, ENISA, January 2018
- Security researchers have revealed some IoT devices and connected cars will survive being wiped and may leak sensitive information when exchanged. Source: “IoT devices leak previous owners' data”, February 2017, https://www.iottechnews.com/news/2017/feb/20/connected-cars-and-iot-devices-leak-previous-owners-data/
- A North-American casino installed a high-tech fish tank as an attraction for its customers. This fish tank used advanced sensors that automatically regulated temperature, salinity and feeding schedules. A hacker gained access to the fish tank and managed to copy 10GB of data from the casino network to which the fish tank was connected. Source: DarkTrace Global Threat Report, 2017, www.darktrace.com
- Researchers at Virginia Tech University and Dashlane analysts have carried out one of the largest empirical studies on password reuse and modification patterns. After examining a database of over 28 million users and their 61 million passwords, they uncovered an alarming figure: 52% of the users studied have the same passwords (or very similar and easily hackable ones) for different services. Source: “The Next Domino to Fall: Empirical Analysis of User Passwords across Online Services”, March 2018, https://people.cs.vt.edu/gangwang/pass
- The 2016 Dyn cyberattack took place on October 21, 2016, and involved multiple distributed denial-of-service attacks (DDoS attacks) targeting systems operated by Domain Name System (DNS) provider Dyn, which caused major Internet platforms and services to be unavailable to large swathes of users in Europe and North America. According to business risk intelligence firm FlashPoint and Akamai Technologies, the attack was a botnet coordinated through a large number of Internet of Things-enabled (IoT) devices, including cameras, residential gateways, and baby monitors, that had been infected with Mirai malware. Source: https://en.wikipedia.org/wiki/2016_Dyn_cyberattack
- https://www.pentestpartners.com/security-blog/hacking-kettles-extracting-plain-text-wpa-psks-yes-really/
- “EMV Security Guidelines: EMVCo Security Evaluation”, EMVCo, LLC, June 2016
- Earl Perkins, Ruggero Contu, Saniye Burcu Alaybeyi, “Five Disturbing Trends in IoT Security for 2018, and What You Can Do About Them”, Gartner, June 2018
 Dirk-Jan Out is the CEO of Brightsight, the number one security lab in the world with over 180 security evaluators. Dirk-Jan was co-editor of the CC and CEM and supported the setting up of several security schemes. His focus is on improving the time-to-market of CC, payment and IoT security evaluations. Brightsight has over 35 years of experience and is recognized by 9 CC schemes and over 25 other schemes such as EMVCo and PCI-SSC.
Dirk-Jan Out is the CEO of Brightsight, the number one security lab in the world with over 180 security evaluators. Dirk-Jan was co-editor of the CC and CEM and supported the setting up of several security schemes. His focus is on improving the time-to-market of CC, payment and IoT security evaluations. Brightsight has over 35 years of experience and is recognized by 9 CC schemes and over 25 other schemes such as EMVCo and PCI-SSC.
 Carlos Serratos, Director Business Development at Brightsight, is a specialist in IoT and compliance. His working experience spans over four continents in the retail, financial and health markets. Before Brightsight, Carlos worked for more than 20 years for Japanese corporations, developing solutions for transaction points and managing projects and workgroups in the areas of fraud prevention and standardization. He is passionate about addressing digital trust as a business enabler to facilitate operations in the digital world.
Carlos Serratos, Director Business Development at Brightsight, is a specialist in IoT and compliance. His working experience spans over four continents in the retail, financial and health markets. Before Brightsight, Carlos worked for more than 20 years for Japanese corporations, developing solutions for transaction points and managing projects and workgroups in the areas of fraud prevention and standardization. He is passionate about addressing digital trust as a business enabler to facilitate operations in the digital world.
 Wouter Slegers is the CEO of TrustCB, the commercial certification body building and operating dedicated certification schemes with predictably short time to certification. Wouter is an IEEE professional member, ACM Senior member, JHAS secretary, and ISCI WG1 subgroup leader. He was instrumental in many of the world’s first certifications of innovative products and is a longtime driver of worldwide methodology and scheme improvements, all keeping high assurance at ever shorter times to certification. His motto for these approaches is “trust and verify”.
Wouter Slegers is the CEO of TrustCB, the commercial certification body building and operating dedicated certification schemes with predictably short time to certification. Wouter is an IEEE professional member, ACM Senior member, JHAS secretary, and ISCI WG1 subgroup leader. He was instrumental in many of the world’s first certifications of innovative products and is a longtime driver of worldwide methodology and scheme improvements, all keeping high assurance at ever shorter times to certification. His motto for these approaches is “trust and verify”.
Sign Up for IoT Technical Community Updates
Calendar of Events
IEEE 8th World Forum on Internet of Things (WF-IoT) 2022
26 October-11 November 2022
Call for Papers
IEEE Internet of Things Journal
Special issue on Towards Intelligence for Space-Air-Ground Integrated Internet of Things
Submission Deadline: 1 November 2022
Special issue on Smart Blockchain for IoT Trust, Security and Privacy
Submission Deadline: 15 November 2022
Past Issues
September 2022
July 2022
March 2022
January 2022
November 2021
September 2021
July 2021
May 2021
March 2021
January 2021
November 2020
July 2020
May 2020
March 2020
January 2020
November 2019
September 2019
July 2019
May 2019
March 2019
January 2019
November 2018
September 2018
July 2018
May 2018
March 2018
January 2018
November 2017
September 2017
July 2017
May 2017
March 2017
January 2017
November 2016
September 2016
July 2016
May 2016
March 2016
January 2016
November 2015
September 2015
July 2015
May 2015
March 2015
January 2015
November 2014
September 2014


