Augmenting Software Engineering Processes Towards Designing Privacy-Aware Internet of Things Applications
The design and development process for the Internet of Things (IoT) applications is more complicated than for desktop, mobile, or web applications. IoT applications require both software and hardware to work together across multiple different types of nodes (e.g. microcontrollers, system-on-chips, mobile phones, miniaturized single board computers, cloud platforms) with different capabilities under different conditions.
IoT applications typically collect and analyze personal data that can be used to derive sensitive information about individuals. Without proper privacy protections in place, IoT applications could lead to serious privacy violations. Thus far, privacy concerns have not been explicitly considered in software engineering processes when designing and developing IoT applications, partly due to a lack of tools, technologies, and guidance. In this newsletter, argues the importance of developing a privacy-aware IoT application design tool to address the challenges mentioned above. This tool should not only transform IoT application designs into privacy-aware application designs but also validate and verify them. We outline how this proposed tool should work in practice and its core functionalities. We also identify research challenges and potential directions towards developing the proposed tool. We anticipate that this proposed tool will save many engineering hours which engineers would otherwise need to spend on developing privacy expertise and applying it. We also highlight the usefulness of this tool towards privacy education and privacy compliance. Let us introduce an example to make our argument more concrete.
A Walking Through Example
Let us consider a simplified use case scenario to highlight the challenges in designing privacy-aware IoT applications. A doctor needs an IoT application which can be used to monitor patients’ rehabilitation process. This use case is inspired by a real-world application called ‘MyPhysioapp’ (myphysioapp.com) [1]. A doctor has compiled his functional requirements as follows. The doctor has difficulties in seeing his patients frequently due to different reasons (e.g., traveling distance, work schedules, etc.). Further, frequent in-person consultations are not necessary for most circumstances. Each in-person visit costs for both the doctor (government) and the patient. Once the initial consultation is performed, the doctor only needs to track the patient's progress and does not need to meet the patient unless there is something exceptional happened. The doctor is only interested in tracking the patient's progress. After evaluating the progress every two weeks, the doctor may ask his specialty nurse to change the exercise plan as necessary. Two software engineers have come up with two different designs as follows to fulfill the above functional requirements. The designs are visually illustrated in Figure 1.
- Design 1: In this design, wearable sensors are used to capture raw data (e.g., accelerometers, gyroscopes) that can be used to identify users’ (patients) activities. Data is then sent to the cloud for activity recognition using a mobile phone as an intermediary device. Next, the cloud services are used to process the raw data and in order to identify the user’s activity patterns. User activity patterns are then compared with doctors recommended a rehabilitation plan to produce a progress report. The doctor can review the progress and make recommendations to the nurse regarding any alterations.
- Design 2: In this design, wearable sensors are not only used to capture raw data but also to identify activities (using the micro-controllers attached to the wearable). Timestamped activities are then sent to the mobile phone. The nurse, based on the doctors’ recommendations, creates the exercise plan and sends it to the patient’s mobile phone. The mobile phone then compares the timestamped activity data and the exercise plan in order to determine how well the patient is performing the exercises. The mobile phone sends a weekly progress report to the doctor. Based on the report, the doctor gives advice to the nurse and she alters the exercise plan accordingly.
It is important to note that both designs satisfy the doctor’s functional requirements. However, design 2 is certainly ‘better’ than design 1 in terms of privacy awareness. Based on this use case scenario, we extract two research questions as follows:
We consider privacy as a trade-off function. Applying a certain privacy-preserving measure into a certain IoT application may impact the implementations in terms of costs, complexity, usability, fault tolerance, responsiveness, etc. Therefore, our aim is not to prescribe a certain design over others. Instead, we want the developer to be informed about privacy-by-design choices before they make their final design decisions. In this regard, we propose a usable privacy-aware IoT application design tool that will inform the privacy-aware design choices to the developers. Previous investigations have shown that applying privacy principles into IoT applications is time-consuming and difficult [2].
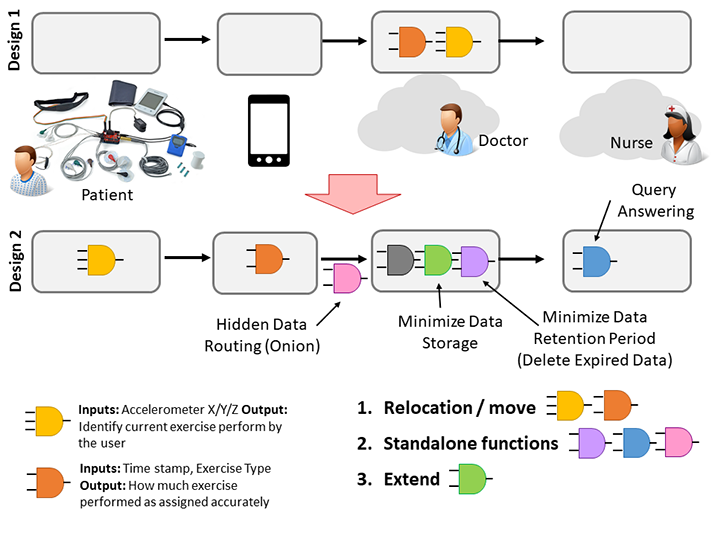
Figure 1: Motivational Scenario: Different IoT application designs can be developed to fulfill the same functional requirements with different privacy risks associated with them.
Target Roles and Audience
We believe such a tool can be beneficial to different types of stakeholders as follows:
- Design Tool for Software Engineers (designers/architects): Primary stakeholders of this tool would be software engineers. We expect them to use this tool to sketch their potential IoT application designs and get validated before moving to the implementation phase. This tool will provide different types of suggestions which engineers can use to improve their IoT application designs in terms of privacy.
- Compliance Tool: This tool will also be useful to demonstrate certain compliance needs (e.g., General Data Protection Regulation (GDPR)). It will have the capability to automatically generate a compliance report for each IoT application design briefly explaining the design decisions and risks associated with, so the compliance officers can determine whether to approve or not.
- Education and Awareness Tool: We also expect this tool to be used for enhancing privacy awareness among students from school level to university level. Over the last few years, there have been many program environments and languages been developed to help young children to learn how to code (tynker.com, scratch.mit.edu).
Tool-Assisted Privacy-Aware IoT Applications Design
The tool we propose is something that the engineering community has not seen before. However, it is inspired by many existing tools used by the engineering community (e.g., UML design tools). First, let us illustrate how the proposed tool (and underline technology) is expected to work in practice using Figure 2. (Step 1) Software engineers will draw their application designs using a pre-defined set of notations. Key components will be nodes (device profiles) and data flows. To ease the process, common device profiles will be provided. This process will look like a UML diagram design process. (Step 2) Engineers will then specify the service which they plan to run. (Step 3) They can either assign each service to a node or just leave them unassigned for the algorithms to do that in a later step. (Step 4/5) Optionally, engineers can provide additional information related to data management (e.g. 90 days of data retention) and context (e.g. healthcare domain). Additional information will help the algorithms to better design IoT applications. The rest of the steps are invisible to engineers and triggered by a single click. (Step 6) Algorithms automatically assign each service into nodes appropriately by considering device capabilities, runtime requirements of the services, and other relevant context information. (Step 7) Algorithms incorporate privacy protection features into the design. This step may also reassign the services into different nodes, if necessary. This is one of the key features of this tool. (Step 8) Algorithms examine the privacy awareness at both node and composition levels.
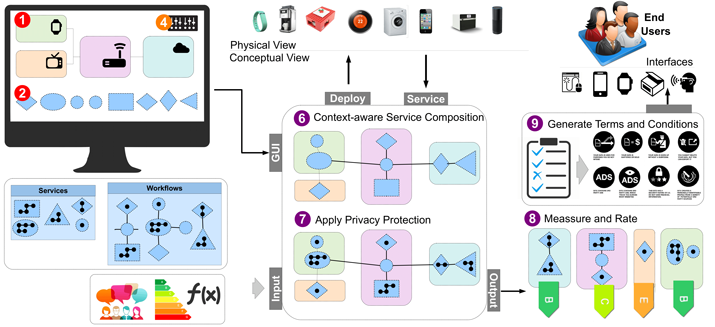
Figure 2: The Workflow of the Proposed Tool.
Then, all the results will be combined to produce the overall privacy index and presented to the engineers. Engineers may consider changing their initial designs to improve the privacy index. (Step 9) The terms and conditions unique for each IoT application design are automatically generated.
Research Directions
We identify three themes of research challenges: (1) Design Notations and User Interactions, (2) Context-Aware Planning and Adaptation, and (3) Operationalisation, Measuring and Rating:
- Design Notations and User Interactions: We envision this tool to follow the visual programming paradigm [3]. The proposed tool is expected to be used by engineers to design IoT applications by manipulating program elements graphically. We expect such a design process would be natural for engineers as they are typically familiar with the design approach such as Unified Modelling Language (UML) and Data Flow Diagrams (DFD). Such familiarity will help engineers to quickly familiarize themselves with the tool. Ideally, the visual programming language will be inspired by the data flow diagrams notations. However, it is important to note that DFDs are flexible enough to be represented in different levels of complexities. Therefore, it would be a fine balance between maintaining simplicity while allowing engineers to design their systems in detail. In addition to the DFD based information, the tool should have ways to gather other related contextual information.
- Context-Aware Planning and Adaptation: The design and development of IoT applications require both software and hardware to work together across multiple different types of nodes (e.g., micro-controllers, system-on-chips, mobile phones, miniaturized single-board computers, cloud platforms) with different capabilities under different conditions (e.g., CPU, memory, energy, data communication, knowledge availability, energy limitations, latency tolerance limitations, domain requirements). Therefore, the privacy-preserving techniques that can be applied on a given node vary depending on the context. The question that needs to be answered is ‘How do we optimally allocate responsibilities to each node based on the context when designing a privacy-aware IoT application?’.
- Operationalization, Measuring, and Rating: Finally, the challenge is how engineers know, given an IoT application design, whether it is a good design or a bad design (from a privacy perspective). We tend to understand different types of measuring and rating/indexing techniques well (e.g. Body Mass Index, energy ratings, food reference intake and so on). However, no such mechanism is available to measure the privacy awareness of IoT applications. We believe such mechanisms (e.g., privacy index) would be increasingly important for both engineers and end-users.
References
- S. Cowan, “My Physio App: Better communication, understanding and results,” Br. J. Sports Med., vol. 50, no. 21, pp. 1348–1349, 2016.
- C. Perera, M. Barhamgi, A. K. Bandara, M. Ajmal, B. Price, and B. Nuseibeh, “Designing Privacy-aware Internet of Things Applications,” Inf. Sci. (Ny)., vol. 512, pp. 238–257, Mar. 2020.
- K. Zhang, D.-Q. Zhang, and J. Cao, “Design, construction, and application of a generic visual language generation environment,” IEEE Trans. Softw. Eng., vol. 27, no. 4, pp. 289–307, 2001.
 Charith Perera is a Lecturer at Cardiff University, UK. He received his BSc (Hons) in Computer Science from Staffordshire University, UK and MBA in Business Administration from the University of Wales, Cardiff, UK and Ph.D. in Computer Science at The Australian National University, Canberra, Australia. Previously, he worked at the Information Engineering Laboratory, ICT Centre, CSIRO. His research interests are the Internet of Things, Sensing as a Service, Privacy, Middleware Platforms, and Sensing Infrastructure. He is a member of IEEE and ACM. Contact him at www.charithperera.net charith.perera@ieee.org
Charith Perera is a Lecturer at Cardiff University, UK. He received his BSc (Hons) in Computer Science from Staffordshire University, UK and MBA in Business Administration from the University of Wales, Cardiff, UK and Ph.D. in Computer Science at The Australian National University, Canberra, Australia. Previously, he worked at the Information Engineering Laboratory, ICT Centre, CSIRO. His research interests are the Internet of Things, Sensing as a Service, Privacy, Middleware Platforms, and Sensing Infrastructure. He is a member of IEEE and ACM. Contact him at www.charithperera.net charith.perera@ieee.org
 Mahmoud Barhamgi is an Associate Professor of computer science at Claude Bernard University Lyon 1. His research focuses on security and privacy preservation in service-oriented architecture, web, and cloud environments. Barhamgi received a Ph.D. in information and communication technology from Claude Bernard University Lyon 1. Contact him at mahmoud.barhamgi@univ-lyon1.fr
Mahmoud Barhamgi is an Associate Professor of computer science at Claude Bernard University Lyon 1. His research focuses on security and privacy preservation in service-oriented architecture, web, and cloud environments. Barhamgi received a Ph.D. in information and communication technology from Claude Bernard University Lyon 1. Contact him at mahmoud.barhamgi@univ-lyon1.fr
Sign Up for IoT Technical Community Updates
Calendar of Events
IEEE 8th World Forum on Internet of Things (WF-IoT) 2022
26 October-11 November 2022
Call for Papers
IEEE Internet of Things Journal
Special issue on Towards Intelligence for Space-Air-Ground Integrated Internet of Things
Submission Deadline: 1 November 2022
Special issue on Smart Blockchain for IoT Trust, Security and Privacy
Submission Deadline: 15 November 2022
Past Issues
September 2022
July 2022
March 2022
January 2022
November 2021
September 2021
July 2021
May 2021
March 2021
January 2021
November 2020
July 2020
May 2020
March 2020
January 2020
November 2019
September 2019
July 2019
May 2019
March 2019
January 2019
November 2018
September 2018
July 2018
May 2018
March 2018
January 2018
November 2017
September 2017
July 2017
May 2017
March 2017
January 2017
November 2016
September 2016
July 2016
May 2016
March 2016
January 2016
November 2015
September 2015
July 2015
May 2015
March 2015
January 2015
November 2014
September 2014


