Fostering Authentication and Authorization in the Social IoT through MQTT-Auth
The Internet of Things (IoT) is becoming more and more an integrated system of intelligent devices, electrical appliances, personal computers, servers, embedded boards, and so on, endowed with well-defined and standardized communication protocols.
These standard communication paradigms are powerful drivers allowing IoT devices to communicate directly with the external world, as well as to participate in communities of objects, to create groups of interest, and to take collaborative actions with the objective to facilitate service and information discovery for both machines and human beings [1]. These capabilities are driving more and more the IoT towards the so-called “social IoT”, an actual social network of intelligent objects with the establishment of direct relationships across smart devices themselves [2,3]. These relationships can be of various kinds:
- co-location, between objects used always in the same place;
- co-working, between object collaborating to provide a common application;
- same ownership of the objects;
- membership of the same production batch,
and can be used to establish direct machine-to-machine interactions, consume services from other devices, advertise services and use offered resources to realize complex services in favor of human beings [4].
On the other hand, this growing consciousness and awareness of the smart objects should be carefully monitored since the security of their services, or of the data they manage, is an everlasting issue. In fact, in the last years, large Distributed Denial of Service (DDoS) attacks took place, with unprecedented volumes of data used to knock-down various Internet services directly or indirectly connected to IoT devices. A well-known example is the Mirai malware, specifically designed to attack and hijack IoT devices and to transform them into bots, afterward exploitable to carry out coordinated attacks [5].
MQTT (Message Queue Telemetry Transport) [6] is a lightweight publish-subscribe messaging protocol, which is rapidly becoming a de facto standard for many IoT communications. It is mainly designed for Machine-to-Machine (M2M) communications, even if it is employed also by the popular Facebook Messenger, due to its very low computation load, particularly appropriate for resource-constrained environments. MQTT works well also in not reliable scenarios, i.e., with limited bandwidth and high latency, since it can guarantee the delivery of messages to all subscribers. Its inherent simplicity, support for QoS, lack of complex management and flexible payload format make it suitable for every IoT and social IoT scenario.
Unfortunately, MQTT specification does not include any security-related mechanism, apart from an optional authentication by means of username and password. This security lack, if not filled during the deployment by means of ad-hoc mechanisms (e.g., establishing IPSec VPNs or TLS connections), may lead to some system vulnerabilities. For this reason, proper security solutions for MQTT are expected in order to guarantee an adequate level of security in terms of authentication, authorization, and confidentiality.
Authentication and Authorization for MQTT
MQTT-TLS profile of ACE (Authentication and Authorization for Constrained Environments) [7] is a recent Internet draft trying to set up a standard for endowing MQTT with authentication and authorization capabilities. However, it is based on an Authorization Server for communicating the tokens to the broker and to the clients (either publishers or subscribers); moreover, it relies upon TLS for guaranteeing confidentiality, possibly adding implementation complexity.
When considering a more decentralized and distributed scenario, like the one of the social IoT, a lightweight solution, called MQTT-Auth, has been recently proposed [8] [9].
MQTT-Auth exploits the AugPAKE algorithm [10] for guaranteeing confidentiality. It also uses two novel tokens, one to authenticate the creation and the publishing on a certain topic at the broker side, and a second one to authorize access to a specific topic on the part of other, trusted, subscribers. These tokens can be also applied to a hierarchy of topics by means of wildcards, i.e., symbols replacing explicit topics.
The usage of the tokens is transparent on the point of view of the broker, which is unaware, in advance, of the legitimate topics and subscribers. The broker has only to create an AuthenticationTopic and a temporary topic, named after the ClientID, to allow for the AugPAKE message exchange.
The authorization token, needed to access data coming from the publishers on a particular topic, is transferred to the legitimate subscribers through a secure side channel. This side channel, in the proposed versions of MQTT-Auth, is a direct visual channel in which the authorization token is displayed, for example, in the form of a QR code.
MQTT-Auth requires very few modifications, with respect to standard MQTT, since it permits to directly encapsulate AugPAKE messages, as well as the novel tokens, directly in the fields of standard MQTT messages.
MQTT Authentication and Authorization in the Social IoT
One key point in MQTT-Auth is the possibility to exchange a piece of information (the Auth2 token), through a secondary secure channel. In the original proposal, only a visual means like a readable token or QR code are indicated as examples.
However, in case of social IoT, other mechanisms can be successfully used as a secure side channel, in particular exploiting the social relations amongst participants. On the other hand, social IoT scenarios, where devices have to communicate trustworthily with each other, in an ecosystem where there is the chance that no human interactions take place, may benefit from an authorization mechanism like MQTT-Auth.
The foreseen advantages of combining the two systems could be summarized as follows:
- Automated and distributed confidentiality and authorization capabilities: smart objects can socially interact with each other leveraging on MQTT-Auth to exchange securely data across themselves. The confidentiality of the transmitted data is guaranteed by the encryption with the secret key defined through the AugPAKE procedure, while the guarantee that only certain authorized devices can access the data, or part of the data of a hierarchy of topics, is ensured by the usage of the authorization token.
- Automated and distributed authenticity of the data: thanks to the authentication token, social smart object interacting by means of MQTT-Auth could be sure that only legitimate devices produced the consumed data or services.
- Exploitation of trusted social relationships: some of the aforementioned social relationships among smart objects could be effectively used to transfer MQTT-Auth authorization token from a publishing device to any, trusted, potential subscribing objects. For instance:
- devices produced in the same batch could have a pre-shared secret key used to communicate securely the authorization token;
- co-located devices could use short-range technologies (i.e., NFC or VLC) to exchange securely the authorization token authorization token;
- co-working objects may exploit other, already existing, secure communication channels to exchange the authorization token.
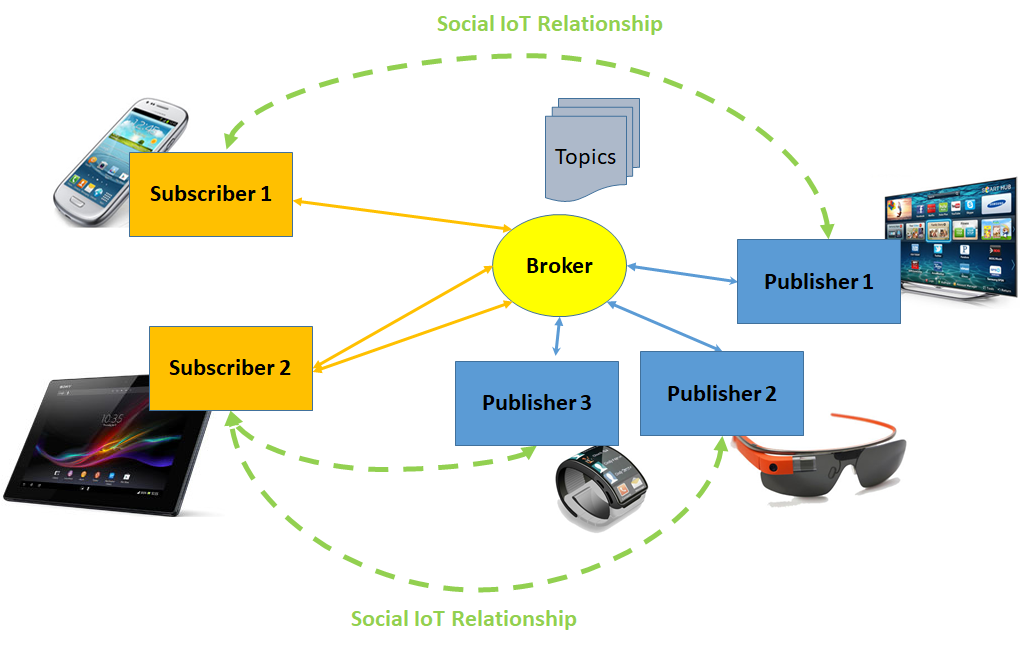
Figure 1: MQTT-Auth in a social IoT environment.
Figure 1 shows a social IoT scenario, where publishing and subscribing smart objects exploit social IoT relationships for setting up a secure side channel used to exchange the MQTT-Auth authorization token.
Despite the aforementioned benefits and advantages, some challenges are still to be resolved to deploy effectively MQTT-Auth for a social IoT scenario. First, the discovery and choice of the most suitable social relationship to exploit for transmitting the authorization token. This and the degree of trustworthiness of the relationships may change over time causing possible periods of out-of-service in case the trust of certain devices towards other companions decreases under a certain critical threshold. Second, the possible need of multiple brokers in order for the social smart objects to compose a complex service. There is the possibility to federate brokers in MQTT specifications, but the application of MQTT-Auth to bridging or clustering techniques, involving many brokers, has not yet been studied or analyzed, to the best of our knowledge. Third, smart social objects have to be endowed with hardware capable of performing in a lightweight way, the operations involved in all MQTT-Auth phases, i.e., the creation of the shared secret key through the AugPAKE procedure, and authenticated encryption with AES and at least a 256-bit key.
Acknowledgments
The authors want to thank Prof. Massimo Vecchio for the fruitful insights regarding the security in MQTT, Mr. Marco Calabretta for developing the running code of MQTT-Auth and Mr. Giovanni Perrone for the help in enlightening some useful details of MQTT standard.
References
- B. H. Phuc, P. Van Quang, N. Q. Linh, and P. Van Huong, "Dynamic Threading to Improve Embedded Software Performance in IoT Devices Using MQTT Protocol," 2018 International Conference on Advanced Technologies for Communications (ATC), Ho Chi Minh City, Vietnam, 2018, pp. 321-325.
- Luigi Atzori, Antonio Iera, Giacomo Morabito, “Understanding the Internet of Things: definition, potentials, and societal role of a fast evolving paradigm”, Ad Hoc Networks, Volume 56, pp. 122-140, 2017.
- L. Atzori et al., "Social-IoT Enabled Identifier/Locator Splitting: Concept, Architecture, and Performance Evaluation," 2018 IEEE International Conference on Communications (ICC), Kansas City, MO, 2018, pp. 1-6.
- R. Pecori, “Internet of Things toward Social IoT”, keynote speech at the special session on Communications, Security and Data Analysis in the Social Internet of Things, ISWCS 2017, Bologna, Italy.
- Perrone G., Vecchio M., Pecori R. and Giaffreda R., “The Day After Mirai: A Survey on MQTT Security Solutions After the Largest Cyber-attack Carried Out through an Army of IoT Devices,” in Proceedings of the 2nd International Conference on Internet of Things, Big Data and Security - Volume 1: IoTBDS 2017.
- MQTT Version 5.0 specifications. Available at: http://docs.oasis-open.org/mqtt/mqtt/v5.0/mqtt-v5.0.html. Accessed: January, 2018.
- MQTT-TLS profile of ACE, IETF Internet draft, available at https://tools.ietf.org/html/draft-sengul-ace-mqtt-tls-profile-03, October 2018.
- M. Calabretta, R. Pecori and L. Veltri, "A Token-based Protocol for Securing MQTT Communications," 2018 26th International Conference on Software, Telecommunications and Computer Networks (SoftCOM), Split, Croatia, 2018, pp. 1-6.
- M. Calabretta, R. Pecori, M. Vecchio, L. Veltri, "MQTT-Auth: a Token-based Solution to Endow MQTT with Authentication and Authorization Capabilities", Journal of Communications Software and Systems. Volume 14, issue 4, pp. 320-331, 2018.
- S. H. Shin and K. Kobara, “Efcient Augmented Password-Only Authentication and Key Exchange for IKEv2,” IETF RFC 6628, Experimental, June 2012. Available at https://tools.ietf.org/rfc/rfc6628.txt
 Riccardo Pecori got his Ph.D. in Information Technology from the University of Parma in 2011. He has been Adjunct Professor of various courses regarding telecommunication networks, informatics, didactics of telecommunications, cybersecurity for both University of Parma and eCampus University. Since 2015 he has been Assistant Professor of Computer Science at eCampus University teaching Computer Security, Network Security, and the Internet of Things. He is editor of “Future Generation Computer Systems” and has been TPC member of various conferences about computer science and telecommunications, organizing also a special session on “Social Internet of Things” at ISWCS 2017. His research interests regard network security, security in the Internet of Things, educational and social Big Data analysis.
Riccardo Pecori got his Ph.D. in Information Technology from the University of Parma in 2011. He has been Adjunct Professor of various courses regarding telecommunication networks, informatics, didactics of telecommunications, cybersecurity for both University of Parma and eCampus University. Since 2015 he has been Assistant Professor of Computer Science at eCampus University teaching Computer Security, Network Security, and the Internet of Things. He is editor of “Future Generation Computer Systems” and has been TPC member of various conferences about computer science and telecommunications, organizing also a special session on “Social Internet of Things” at ISWCS 2017. His research interests regard network security, security in the Internet of Things, educational and social Big Data analysis.
 Luca Veltri is an assistant professor at the Department of Engineering and Architecture of the University of Parma, teaching classes on Communication Networks, and Network Security. From 1999 to 2002, before joining the University of Parma, he has been with CoRiTeL, a research consortium founded by Ericsson Telecomunicazioni, where he led different research projects in networking and multimedia communications. He participated also in several research projects funded by the European Union, by the European Space Agency, and by the Italian Ministry of University and Research. His current research interests include Internet of Things, Software-Defined Networking, and Network Security. He is a co-author of more than 70 papers on international conferences and journals.
Luca Veltri is an assistant professor at the Department of Engineering and Architecture of the University of Parma, teaching classes on Communication Networks, and Network Security. From 1999 to 2002, before joining the University of Parma, he has been with CoRiTeL, a research consortium founded by Ericsson Telecomunicazioni, where he led different research projects in networking and multimedia communications. He participated also in several research projects funded by the European Union, by the European Space Agency, and by the Italian Ministry of University and Research. His current research interests include Internet of Things, Software-Defined Networking, and Network Security. He is a co-author of more than 70 papers on international conferences and journals.
Sign Up for IoT Technical Community Updates
Calendar of Events
IEEE 8th World Forum on Internet of Things (WF-IoT) 2022
26 October-11 November 2022
Call for Papers
IEEE Internet of Things Journal
Special issue on Towards Intelligence for Space-Air-Ground Integrated Internet of Things
Submission Deadline: 1 November 2022
Special issue on Smart Blockchain for IoT Trust, Security and Privacy
Submission Deadline: 15 November 2022
Past Issues
September 2022
July 2022
March 2022
January 2022
November 2021
September 2021
July 2021
May 2021
March 2021
January 2021
November 2020
July 2020
May 2020
March 2020
January 2020
November 2019
September 2019
July 2019
May 2019
March 2019
January 2019
November 2018
September 2018
July 2018
May 2018
March 2018
January 2018
November 2017
September 2017
July 2017
May 2017
March 2017
January 2017
November 2016
September 2016
July 2016
May 2016
March 2016
January 2016
November 2015
September 2015
July 2015
May 2015
March 2015
January 2015
November 2014
September 2014


