IoT and Blockchain Convergence: Benefits and Challenges
The Internet of Things (IoT) as a concept is fascinating and exciting, but one of the major challenging aspects of IoT is having a secure ecosystem encompassing all building blocks of IoT-architecture. Understanding the different building blocks of IoT, identifying the areas of vulnerability in each block and exploring technologies needed to counter each of the weaknesses are essential in dealing with the security issue of IoT.
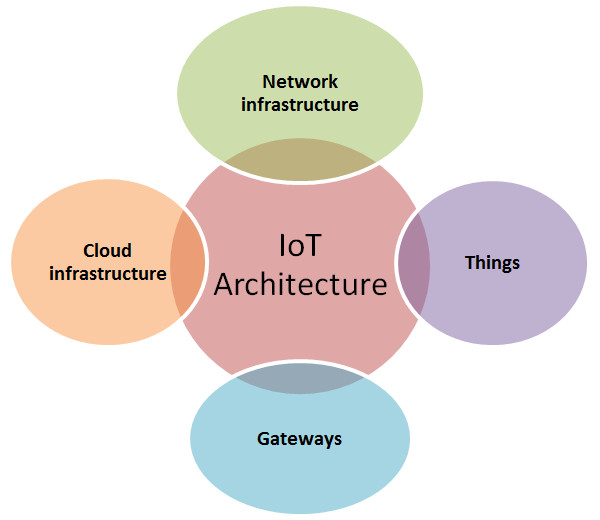
IoT architecture can be represented by four building blocks:
- Things: These are defined as uniquely identifiable nodes, primarily sensors that communicate without human interaction using different connectivity methods.
- Gateways: These act as intermediaries between things and the cloud to provide the needed connectivity, security, and manageability.
- Network infrastructure: This is comprised of routers, aggregators, gateways, repeaters and other devices that control and secure data flow.
- Cloud infrastructure: Cloud infrastructure contains large pools of virtualized servers and storage that are networked together with computing and analytical capabilities.
Challenges to secure IoT deployments
Existing security technologies will play a role in mitigating IoT risks but they are not enough. The goal is to get data securely to the right place, at the right time, in the right format. It's easier said than done for many reasons, and here is a list of some of the challenges:
- Many IoT Systems are poorly designed and implemented, using diverse protocols and technologies that create complex and sometimes conflicting configurations.
- Limited guidance for life cycle maintenance and management of IoT devices
- IoT privacy concerns are complex and not always readily evident.
- There is a lack of standards for authentication and authorization of IoT edge devices.
- Security standards, for platform configurations, involving virtualized IoT platforms supporting multi-tenancy is immature.
- The uses for Internet of Things technology are expanding and changing—often in uncharted waters.
In addition to the above list, new security technologies will be required to protect IoT devices and platforms from both information attacks and physical tampering, to encrypt their communications, and to address new challenges such as impersonating "things" or denial-of-sleep attacks that drain batteries, to denial-of-service attacks (DoS). But IoT security will be complicated by the fact that many "things" use simple processors and operating systems that may not support sophisticated security approaches.
A prime example of the urgent need for such new security technologies is the recent massive distributed denial of service attack (DDoS) that crippled the servers of popular services like Twitter, Netflix, NYTimes, and PayPal across the U.S. on October 21st, 2016. It was the result of an immense assault that involved millions of internet addresses and malicious software. One source of the traffic for the attacks was devices infected by the Mirai malware. The attack comes amid heightened cybersecurity fears and a rising number of internet security breaches. All indications suggest that countless IoT devices that power everyday technology like closed-circuit cameras and smart-home devices were hijacked by the malware, and used against the servers.
The problem with the current centralized model
Current IoT ecosystems rely on centralized, brokered communication models, otherwise known as the server/client paradigm. All devices are identified, authenticated and connected through cloud servers that sport huge processing and storage capacities. Connections between devices have to exclusively go through the internet, even if they happen to be a few feet apart.
While this model has connected generic computing devices for decades and will continue to support small-scale IoT networks as we see them today, it will not be able to respond to the growing needs of the huge IoT ecosystems of tomorrow.
Existing IoT solutions are expensive because of the high infrastructure and maintenance cost associated with centralized clouds, large server farms, and networking equipment. The sheer amount of communications that will have to be handled when there are tens of billions of IoT devices will increase those costs substantially.
Even if the unprecedented economic and engineering challenges are overcome, cloud servers will remain a bottleneck and point of failure that can disrupt the entire network.
Decentralizing IoT networks
A decentralized approach to IoT networking would solve many of the issues above. Adopting a standardized peer-to-peer communication model to process the hundreds of billions of transactions between devices will significantly reduce the costs associated with installing and maintaining large centralized data centers and will distribute computation and storage needs across the billions of devices that form IoT networks. This will prevent failure in any single node in a network from bringing the entire network to a halting collapse.
However, establishing peer-to-peer communications will present its own set of challenges, chief among them the issue of security. And as we all know, IoT security is much more than just about protecting sensitive data. The proposed solution will have to maintain privacy and security in huge IoT networks and offer some form of validation and consensus for transactions to prevent spoofing and theft.
To perform the functions of traditional IoT solutions without a centralized control, any decentralized approach must support three foundational functions:
- Peer-to-peer messaging;
- Distributed file sharing;
- Autonomous device coordination.
The blockchain approach
Blockchain, the "distributed ledger" technology, has emerged as an object of intense interest in the tech industry and beyond. Blockchain technology offers a way of recording transactions or any digital interaction in a way that is designed to be secure, transparent, highly resistant to outages, auditable, and efficient; as such, it carries the possibility of disrupting industries and enabling new business models. The technology is young and changing very rapidly; widespread commercialization is still a few years off. Nonetheless, to avoid disruptive surprises or missed opportunities, strategists, planners, and decision makers across industries and business functions should pay heed now and begin to investigate applications of the technology.
What is blockchain?
Blockchain is a database that maintains a continuously growing set of data records. It is distributed in nature, meaning that there is no master computer holding the entire chain. Rather, the participating nodes have a copy of the chain. It’s also ever-growing — data records are only added to the chain.
A blockchain consists of two types of elements:
- Transactions are the actions created by the participants in the system.
- Blocks record these transactions and make sure they are in the correct sequence and have not been tampered with.
What are some advantages of blockchain?
The big advantage of blockchain is that it's public. Everyone participating can see the blocks and the transactions stored in them. This doesn't mean everyone can see the actual content of your transaction, however; that's protected by your private key.
A blockchain is decentralized, so there is no single authority that can approve the transactions or set specific rules to have transactions accepted. That means there's a huge amount of trust involved since all the participants in the network have to reach a consensus to accept transactions.
Most importantly, it's secure. The database can only be extended and previous records cannot be changed (at least, there's a very high cost if someone wants to alter previous records).
How does it work?
When someone wants to add a transaction to the chain, all the participants in the network will validate it. They do this by applying an algorithm to the transaction to verify its validity. What exactly is understood by "valid" is defined by the blockchain system and can differ between systems. Then it is up to a majority of the participants to agree that the transaction is valid.
A set of approved transactions is then bundled in a block, which gets sent to all the nodes in the network. They, in turn, validate the new block. Each successive block contains a hash, which is a unique fingerprint, of the previous block.
The blockchain and IoT
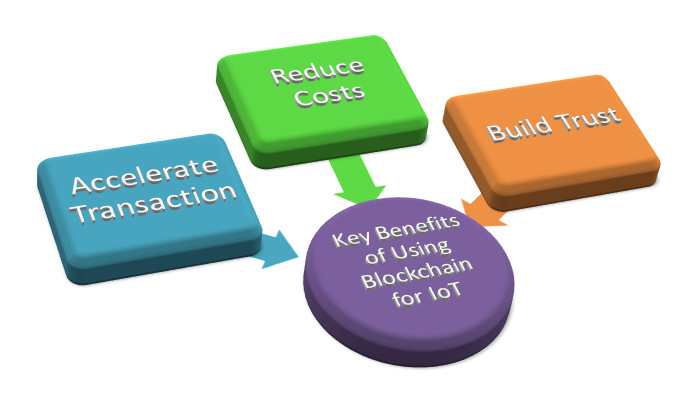
Blockchain technology is the missing link to settle privacy and reliability concerns in the Internet of Things. Blockchain technology could perhaps be the silver bullet needed by the IoT industry. It can be used in tracking billions of connected devices, enabling the processing of transactions and coordination between devices; this allows for significant savings for IoT industry manufacturers. This decentralized approach would eliminate single points of failure, creating a more resilient ecosystem for devices to run on. The cryptographic algorithms used by blockchains would make consumer data more private.
The ledger is tamper-proof and cannot be manipulated by malicious actors because it doesn't exist in any single location, and man-in-the-middle attacks cannot be staged because there is no single thread of communication that can be intercepted. Blockchain makes trustless, peer-to-peer messaging possible and has already proven its worth in the world of financial services through cryptocurrencies such as bitcoin, providing guaranteed peer-to-peer payment services without the need for third-party brokers.
The decentralized, autonomous, and trustless capabilities of the blockchain make it an ideal component to become a foundational element of IoT solutions. It is no surprise that enterprise IoT technologies have quickly become one of the early adopters of blockchain technology.
In an IoT network, the blockchain can keep an immutable record of the history of smart devices. This feature enables the autonomous functioning of smart devices without the need for centralized authority. As a result, the blockchain opens the door to a series of IoT scenarios that were remarkably difficult, or even impossible to implement without it.
For example, by leveraging the blockchain, IoT solutions can enable secure, trustless messaging between devices in an IoT network. In this model, the blockchain will treat message exchanges between devices similar to financial transactions in a bitcoin network. To enable message exchanges, devices will leverage smart contracts which then model the agreement between the two parties.
One of the most exciting capabilities of the blockchain is the ability to maintain a duly decentralized, trusted ledger of all transactions occurring in a network. This capability is essential to enable the many compliances and regulatory requirements of industrial IoT (IIoT) applications without the need to rely on a centralized model.
What are the challenges?
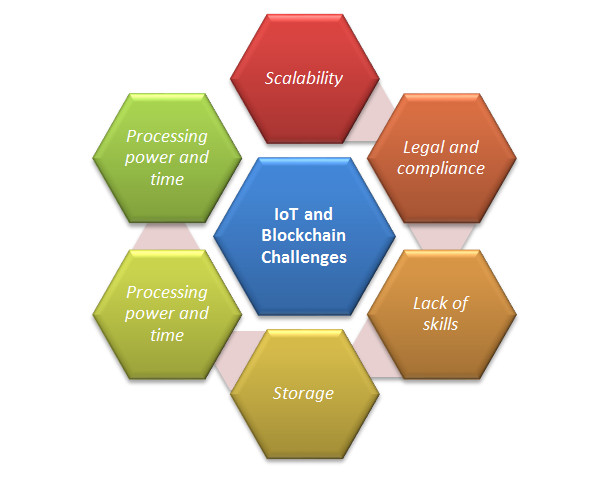
In spite of all its benefits, the blockchain model is not without its flaws and shortcomings:
- Scalability issues pertaining to the blockchain that might lead to centralization, which is casting a shadow over the future of the cryptocurrency.
- Processing power and time required to perform encryption for all the objects involved in a blockchain-based ecosystem. IoT ecosystems are very diverse. In contrast to generic computing networks, IoT networks are comprised of devices that have very different computing capabilities, and not all of them will be capable of running the same encryption algorithms at the desired speed.
- Storage too will be a hurdle. Blockchain eliminates the need for a central server to store transactions and device IDs, but the ledger has to be stored on the nodes themselves. And the ledger will increase in size as time passes. That is beyond the capabilities of a wide range of smart devices such as sensors, which have very low storage capacity.
- Lack of skills: few people understand how blockchain technology really works and when you add IoT to the mix that number will shrink drastically.
- Legal and compliance issues: It's a new territory in all aspects without any legal or compliance code to follow, which is a serious problem for manufacturers and service providers. This challenge alone will scare off many businesses from using blockchain technology.
The optimum platform
Developing solutions for the Internet of Things requires unprecedented collaboration, coordination, and connectivity for each piece in the ecosystem, and throughout the ecosystem as a whole. All devices must work together and be integrated with all other devices, and all devices must communicate and interact seamlessly with connected systems and infrastructures. It's possible, but it can be expensive, time-consuming, and difficult.
The optimum platform for IoT can:
- Acquire and manage data to create a standards-based, scalable, and secure platform.
- Integrate and secure data to reduce cost and complexity while protecting your investment.
- Analyze data and act by extracting business value from data, and then acting on it.
Security needs to be built in as a foundation of IoT systems, with rigorous validity checks, authentication, data verification, and all the data needs to be encrypted. At the application level, software development organizations need to be better at writing code that is stable, resilient and trustworthy, with better code development standards, training, threat analysis and testing. As systems interact with each other, it's essential to have an agreed interoperability standard, which is safe and valid. Without a solid bottom-top structure we will create more threats with every device added to the IoT. What we need is a secure and safe IoT with privacy protected. That's a tough trade off but not impossible and blockchain technology is an attractive option if we can overcome its drawbacks.
Further reading
http://tech.economictimes.indiatimes.com/news/internet/5-challenges-to-internet-of-things/52700940
https://www.spiceworks.com/marketing/reports/iot-trends/
https://techcrunch.com/2016/06/28/decentralizing-iot-networks-through-blockchain/
http://www.blockchaintechnologies.com/blockchain-internet-of-things-iot
https://postscapes.com/blockchains-and-the-internet-of-things/
https://blogs.thomsonreuters.com/answerson/blockchain-technology/
https://www.linkedin.com/pulse/20140403055037-246665791-bitcoin-accepted-here?trk=mp-author-card
https://www.linkedin.com/pulse/securing-internet-things-iot-ahmed-banafa?trk=mp-author-card
 Ahmed Banafa has extensive experience in research, operations and management, with a focus on the IoT area. He is a reviewer and a technical contributor for the publication of several technical books. He served as a faculty member at several well-known universities and colleges, including the University of California, Berkeley; California State University-East Bay; San Jose State University; and University of Massachusetts. He is the recipient of several awards, including Distinguished Tenured Staff Award of 2013, Instructor of the year for 2013, 2014, and Certificate of Honor for Instructor from the City and County of San Francisco. He was named as number one tech voice to follow by LinkedIn in 2016.
Ahmed Banafa has extensive experience in research, operations and management, with a focus on the IoT area. He is a reviewer and a technical contributor for the publication of several technical books. He served as a faculty member at several well-known universities and colleges, including the University of California, Berkeley; California State University-East Bay; San Jose State University; and University of Massachusetts. He is the recipient of several awards, including Distinguished Tenured Staff Award of 2013, Instructor of the year for 2013, 2014, and Certificate of Honor for Instructor from the City and County of San Francisco. He was named as number one tech voice to follow by LinkedIn in 2016.
Sign Up for IoT Technical Community Updates
Calendar of Events
IEEE 8th World Forum on Internet of Things (WF-IoT) 2022
26 October-11 November 2022
Call for Papers
IEEE Internet of Things Journal
Special issue on Towards Intelligence for Space-Air-Ground Integrated Internet of Things
Submission Deadline: 1 November 2022
Special issue on Smart Blockchain for IoT Trust, Security and Privacy
Submission Deadline: 15 November 2022
Past Issues
September 2022
July 2022
March 2022
January 2022
November 2021
September 2021
July 2021
May 2021
March 2021
January 2021
November 2020
July 2020
May 2020
March 2020
January 2020
November 2019
September 2019
July 2019
May 2019
March 2019
January 2019
November 2018
September 2018
July 2018
May 2018
March 2018
January 2018
November 2017
September 2017
July 2017
May 2017
March 2017
January 2017
November 2016
September 2016
July 2016
May 2016
March 2016
January 2016
November 2015
September 2015
July 2015
May 2015
March 2015
January 2015
November 2014
September 2014



Comments
2017-01-11 @ 3:03 AM by Kolli, Chakravarthy
Great article! Agree that centralized IOT systems will not work because of scalability, privacy and security reasons. However I am convinced storage is an issue especially with sensors. This is because I do not expect sensors to be part of the consensus process. A proxy device with enough storage and processing power could be the node that runs consensus for a bunch of sensors.
2017-01-18 @ 1:51 PM by Borjan, Gabor
2017-01-22 @ 1:21 PM by D, Ollencio
Excellent article but it confused me a bit.Why would you suggest that "centralisation" could occur in a block chain distributed topology? We are also suggesting two levels on "networks" are present - one "data" using block chain and the other "physical communications" maybe control, between devices which can be compromised? Maybe I do not know enough about the ecosystem being built around localised sensors but not to have everything including "logging on/off" between devices icluded in the same block chain secure transaction records may not be wise? Also delays in "decision making" because of the constant referral to the local host - appears to be raised as a weakness. Is this true if the systems are localised?